If you run Exchange 2010 and are using Kerberos authentication for Outlook in a load-balanced environment you probably have scheduled the RollAlternateserviceAccountPassword.ps1 script. This script updates the alternate service account credential (ASA credential) and pushes the new value to your CAS servers. Common parameter options are -ToEntireForest, -ToArrayMembers or -CopyFrom with -ToSpecificServers. If you are familiar with the script, I assume they need no clarification.
Now consider a scenario where you used -ToArrayMembers and you add your first Exchange 2013 CAS server to that site. The script uses the Get-ClientAccessArray cmdlet to query the members of this array, this cmdlet returns the Exchange 2013 CAS servers in that site too.
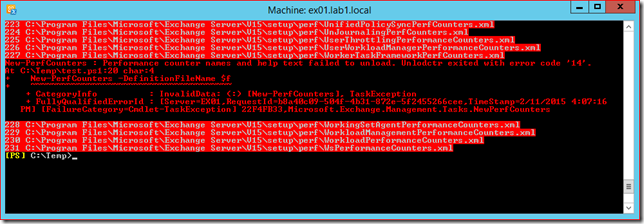
Unfortunately the script is not able to update the ASA credential on both 2010 and 2013 servers. This causes the script to fail when it tries to process the Exchange 2013 CAS server and ultimately cancels the process of updating and synchronizing the ASA credential. Unless you configured specific monitoring for this process you'll probably won't notice the issue before stuff breaks and users start complaining. To check if this issue applies to your environment:
Get-ClientAccessServer -IncludeAlternateServiceAccountCredentialstatus |Fl Name, AlternateServiceAccountConfiguration
By the way, the RollAlternateserviceAccountPassword.ps1 script writes a log file in the $exinstall\Logging\RollAlternateServiceAccountPassword folder. Be ware this log is written on the server where the script is executed, this is not necessarily the server where you scheduled the script to run.
There are several workarounds to prevent this from happening. First you could consider to deploy the Exchange 2013 CAS servers in another site. Another option is to update a single server first and then use the -CopyFrom and -ToSpecificServers switches to update your Exchange 2010 CAS servers which you have to specify.
For more information on planning the migration from Exchange 2010 to Exchange 2013 with regards to Kerberos authentication I recommend this excellent article on the Exchange Team Blog: Exchange 2013 and Exchange 2010 Coexistence with Kerberos Authentication