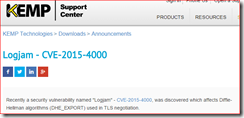
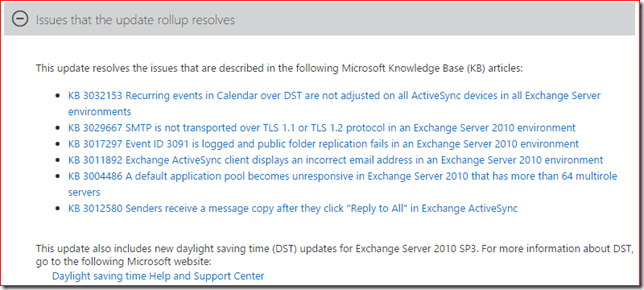
I need to vent, that's all. I'm working with a customer to prepare for the installation of Exchange 2010 SP3 Update Rollup 9. The list of fixed issues is very short and counts only six bullets and a remark about DST updates:
The amazing Rhoderick Milne wrote a post about Exchange 2013 CU and mentioned an ActiveSync issue which involved UR 9 for Exchange 2010 SP3 too.
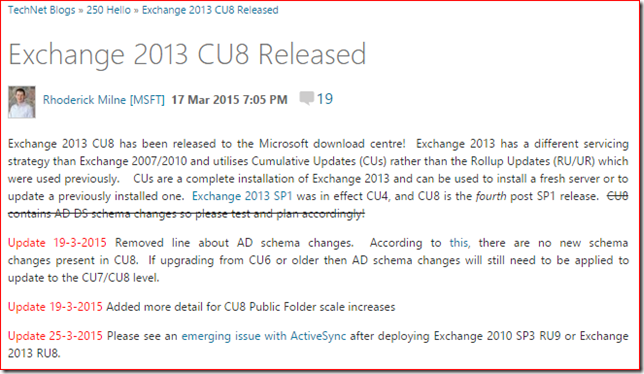
Please see an emerging issue with ActiveSync after deploying Exchange 2010 SP3 RU9 or Exchange 2013 RU8.
The article he refers to is KB3035227: Some Android devices can't set up an Exchange account after you install Exchange Server 2010 SP3 RU9 or Exchange Server 2013 CU8 So there is a known issue with UR9 but it is not included in the Known Issues section of Update Rollup 9 for Exchange Server 2010 Service Pack 3. That's annoying but well, I found the article so let's read...

So we're talking about adding a new ActiveSync (yes, that's one word and not Active Sync like the article says) account and Android fails to complete the Autodiscover process.
In the Cause section is a little bit of explanation about this issue:
Exchange Server 2010 SP3 RU9 and Exchange Server 2013 CU8 contain a new MobileSyncRedirectBypass feature in the Autodiscover service for Android devices. By default, this feature is enabled. Some versions of Android may not understand this feature.
Maybe I'm a bad reader but I still don't understand. What is this "new MobileSyncRedirectBypass feature in the Autodiscover service"? And where in the Autodiscover process will it send a 451 redirect message to the client? And what conditions would trigger this changed behavior?
Luckily there's a link for more information: Exchange ActiveSync Autodiscover is incomplete. The link goes to an article about the Android Activesync implementation and explains that Android does not support the HTTP redirect method which involves a 302 redirect. On the same page we can read that Android does support the 451 redirect. So the "more information" link doesn't answer questions, it raises new questions.
Now have a look at the instructions to disable this new feature. It starts with:
If the MobileSyncRedirectBypass feature is causing the problem, you can turn it off...
Wait, how can we determine that the MobileSyncRedirectBypass feature is causing the problem? Anyway, let's look at the steps:
-
Locate the web.config file for the Autodiscover protocol:
- For Exchange Server 2013 MBX, the file is in the following location:
%ExchangeInstallPath%\ClientAccess\Autodiscover
- For Exchange Server 2010 CAS, the file is in the following location:
%ExchangeInstallPath%\ClientAccess\Autodiscover
- Open the web.config in Notepad, and then change the existing string from "true" to "false."
What existing string? My guess would be MobileSyncRedirectBypass but there's no such string in the file:
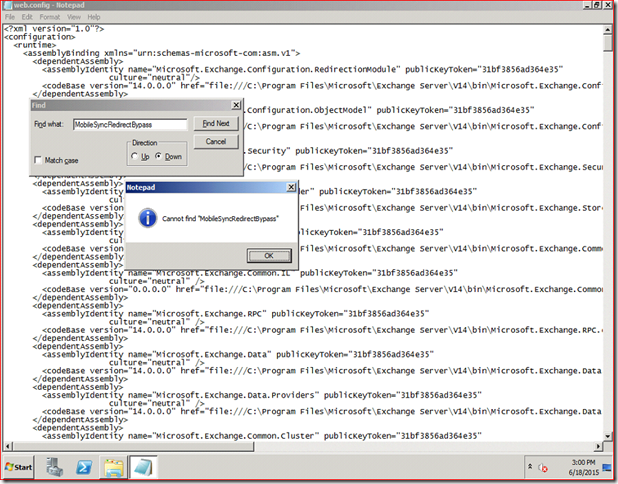
So this article fails to explain the issue or what's causing the issue and the resolution steps are incomplete. And the worst part?
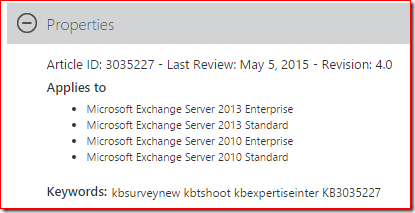
Apparently this is the 4th major revision of the article!
End of rant. Does it make me feel better? Not really. I promise to write a more constructive post once I obtained more information about this issue.